How to Encrypt a VM Using vSphere Encryption
This post will walk through the steps to encrypt a VM using vSphere encryption. Encryption keys are obtained from a deployed Entrust KeyControl v5.4. KMS cluster

To get started here is what you will need to complete the steps in this post:
- A deployed Entrust KeyControl v5.4 cluster (Click this sentence to learn how to do this)
- vCenter and ESXi Host(s) running vSphere 7.x or higher
- Trusted connection between Entrust KeyControl and vCenter (Click this sentence to learn how to do this)
- Powered-off VM
Now, let’s get started…
Select a VM to Encrypt
-
Right click a VM and select VM Policies, Edit VM Storage Policies
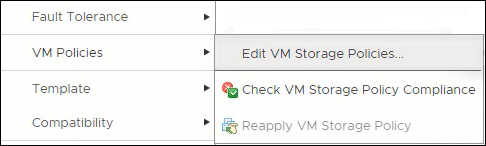
Edit VM Storage Policies
Encrypt the Entire VM?
If you are content with encrypting the entire VM then follow the step in this section.
-
Select VM Encryption Policy from the VM storage policy dropdown list and click OK.
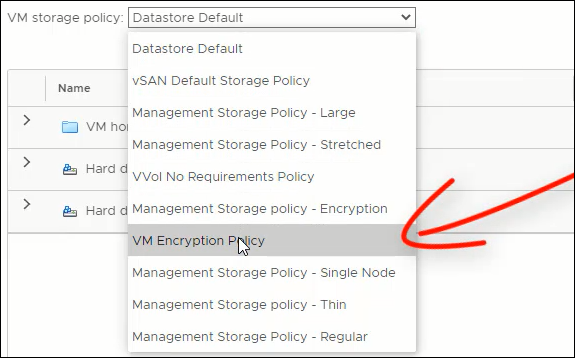
VM Encryption Policy
During this phase vCenter requests an encryption key from KeyControl and presents it to the ESX host where the VM is assigned. This key is referred to as the Key Encryption Key (KEK). The ESX host creates a Data Encryption Key (DEK) and protects it by wrapping the DEK with the KEK. Then the ESX host begins encrypting it.
You can hop over the next section.
Encrypt Individual VMDKs?
If you have a need to encrypt specific VMDKs then follow the steps in this section.
-
Click the Configure per disk slider. It will appear green when per-VMDK selection is enabled.
-
Select VM Encryption Policy from the VM storage policy dropdown list for each VMDK you want to encrypt.
NOTE: You will NOT be able to move past this step if you do not select the same policy for VM Home
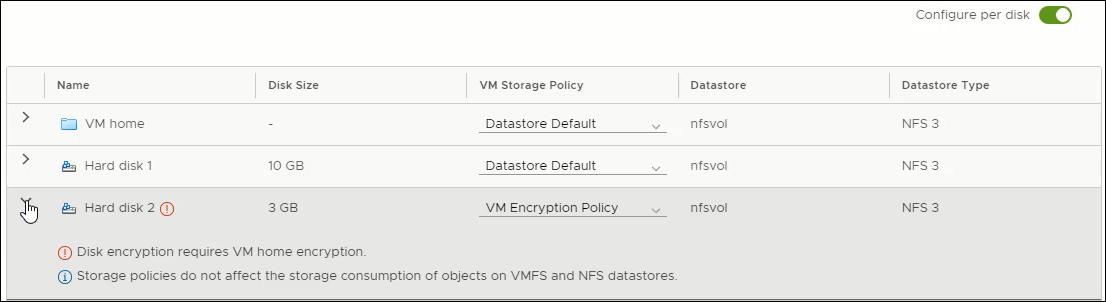
Per VMDK Encryption option
-
After you have selected the VM Encryption Policy for each VMDK and VM Home click OK.
NOTE: You will be required to have the VM powered off.
During this phase vCenter requests an encryption key from KeyControl and presents it to the ESX host where the VM is assigned. This key is referred to as the Key Encryption Key (KEK). The ESX host creates a Data Encryption Key (DEK) and protects it by wrapping the DEK with the KEK. Then the ESX host begins encrypting it.
VM Encryption Done Easily
Once the VM has been encrypted the Encryption status of the VM will state: Encrypted with standard key provider
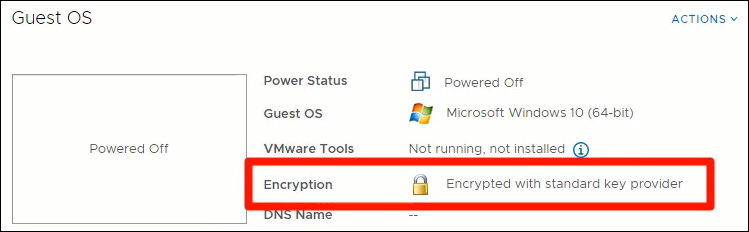
Encrypted VM
Congratulations! You just encrypted a VM using VMware Encryption.
Summary
Let’s summarize what was covered in this post:
- We first confirmed that a 2-node Entrust KeyControl v5.4 cluster had been deployed and connected to vCenter
- Figured out which VM you wanted to encrypt, right-clicked it and edited the VM Storage Policy
- Lastly, you determined if you wanted to encrypt the entire VM or specific VMDKs and waited for encryption to finish
In a follow-on post I will write about how to perform encryption using the Entrust DataControl Policy Agent. Using the Entrust DataControl Policy gent there is no need to power-off the VM.
I hope this post has helped you.
Related Posts
Here are links to related posts:
- Register for a 30-day trial of Entrust KeyControl
- How to deploy a 2-node Entrust KeyControl v5.4 cluster
- How to Connect Entrust KeyControl v5.4 to Active Directory
- How to Add a Another Security Admin to Entrust KeyControl v5.4 from Active Directory
- How to Add Entrust KeyControl v5.4 as a Key Provider in vSphere 7.x
- Entrust KeyControl YouTube playlist
- YouTube video: Entrust KeyControl - Using vSphere Encryption to Encrypt a VM
If there is something you think I’m missing and feel should be added, please let me know.
Thanks for reading!



